TL;DR
Micro Stealer is a Java-based infostealer distributed as fake game downloads. It extracts:
- All browser-saved passwords (Chrome, Firefox, Edge, Brave, Opera)
- Cookies & session tokens for session hijacking
- Discord tokens + injects persistent backdoor into Discord client
- Cryptocurrency wallets (MetaMask, Exodus, Atomic, Electrum, etc.)
- Browser extension data including password managers
- Steam credentials and profile data
Key findings: Anti-recovery tactics block Discord support & Google account recovery. Victims are extorted via WhatsApp and threatened with weaponized false reports if they refuse to pay.
Are You Affected?
You may be a victim if you:
- Downloaded "EldrynWorld", "Crushfall", "Furfall", or "ChurryFall" executables
- Visited
eldrynworld.com and downloaded anything
- Received a Discord DM about "beta testing a game" and ran the file
- Noticed your Discord account locked out or 2FA changed unexpectedly
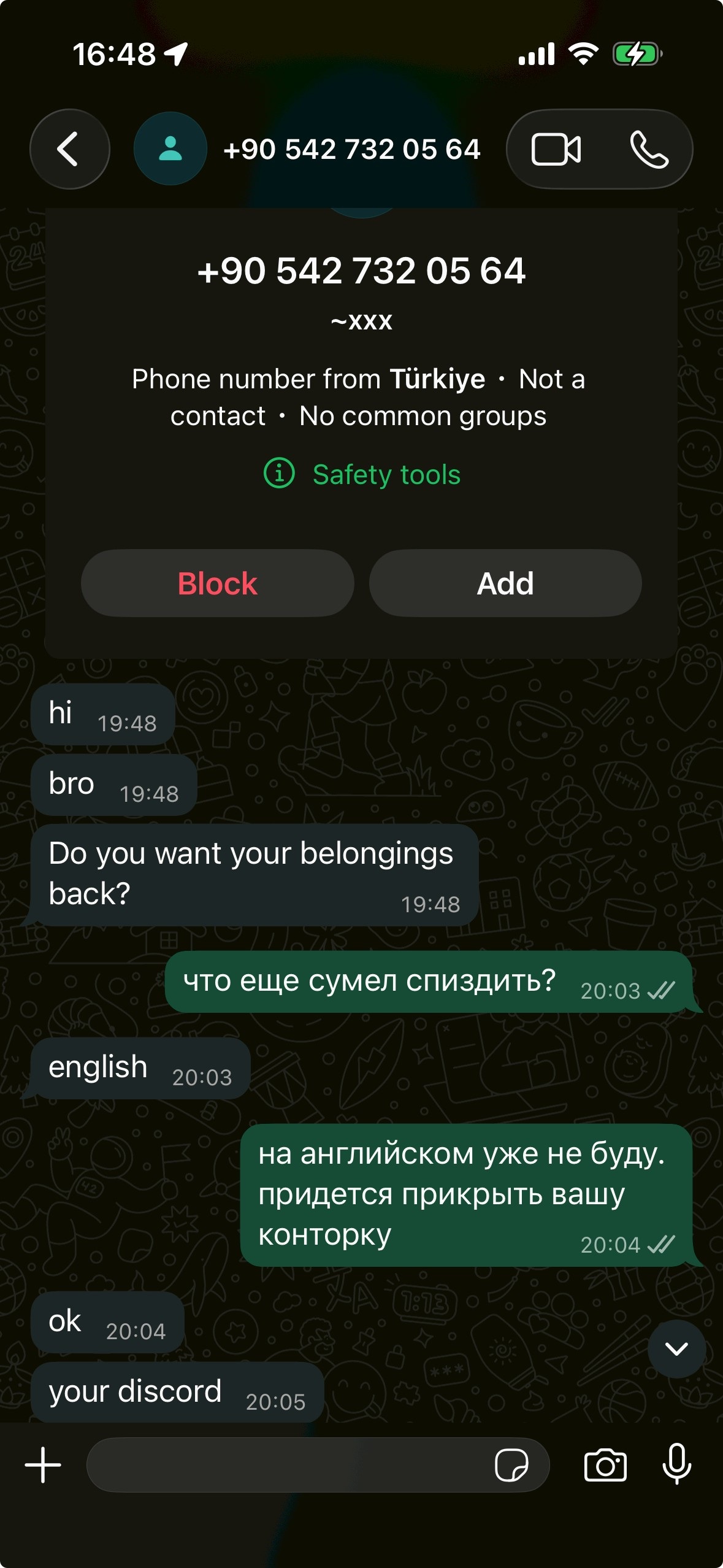
- Received WhatsApp messages asking "Do you want your belongings back?"
Immediate Actions for Victims
1. Discord Account
- Check if you can access support.discord.com — attackers create support accounts with victim emails to block recovery
- If locked out, contact Discord via Twitter/X (@discord) immediately
- Completely uninstall Discord, delete
%APPDATA%\discord, reinstall fresh (client may be injected with malware)
2. Google/Gmail Account
- Check Settings > Personal Info > Birthday (attackers change it to make you appear as a minor)
- Check Settings > Family > Family group (attackers add you to their family as a "child")
- Consider creating your own Family group as a defensive measure
3. All Passwords
- Every password saved in your browser is compromised — reset all of them
- Priority: Email, banking, cryptocurrency, social media
- If you use a browser-extension password manager (Bitwarden, 1Password, LastPass extension, etc.), assume that vault may also be compromised — change your master password from a clean device first
4. System Cleanup
# Remove malware artifacts (PowerShell as Admin)
Remove-Item -Recurse -Force "$env:APPDATA\erkan"
Remove-Item -Force "$env:APPDATA\ysnd.jar"
# Check for persistence
Get-ScheduledTask | Where-Object {$_.TaskPath -like "*erkan*"}
Get-ItemProperty HKCU:\Software\Microsoft\Windows\CurrentVersion\Run
How the Operation Works
Step 1: Social Engineering
Attackers pose as indie game developers on Discord, sending DMs about "beta testing" a platformer game. The malware is disguised as game installers with names like EldrynWorld.exe, Crushfall.exe, Furfall.exe, or ChurryFall.exe.
A professional-looking fake website (eldrynworld.com) adds legitimacy:

The fake eldrynworld.com website featuring a fictional fox platformer game. The "Download Beta" button delivers the malware.
Step 2: Data Exfiltration
Once executed, Micro Stealer harvests everything and uploads it to gofile.io:
- All browser-saved passwords, cookies, and autofill data
- Discord tokens + injects persistent backdoor into Discord client
- Cryptocurrency wallet files (MetaMask, Exodus, Atomic, Electrum, etc.)
- Steam credentials and profile data
- Browser extension data including password manager vaults
A summary of the stolen data is automatically posted to the attackers' Discord server via webhook, alerting them to a new victim.
Step 3: Extortion
Attackers contact victims via WhatsApp from Turkish phone numbers (+90), demanding payment (often in cryptocurrency) in exchange for "leaving them alone" and not exploiting their stolen data further.
Opening line: "Do you want your belongings back?"
Phone: +90 542 732 05 64 (Turkey)
The victim (Russian-speaking) responded: "What else did you manage to steal?" and "I won't speak English anymore. We'll have to shut down your little operation."
Do not pay. There is no guarantee attackers will return access, and payment funds further criminal activity.
Step 4: Account Takeover & Weaponized False Reports
Regardless of whether the victim pays, attackers systematically lock them out of all accounts:
- Discord: Replace 2FA, change password, create a support account with victim's email (blocks recovery tickets)
- Google: Change birthday to make victim appear as a minor, add them to attacker's Google Family as a "child" (parental controls block recovery)
- Email: Use stolen cookies/passwords to access and lock out email accounts
WEAPONIZED FALSE REPORTS: When victims refuse to pay, attackers manufacture evidence of ToS violations (including CSAM solicitation) using the victim's compromised account, then report the victim to Discord. This results in account bans that are extremely difficult to appeal.
→ Read the full case study — a detailed forensic analysis of how this weaponized false report attack destroyed an innocent victim's 11-year-old Discord account.
Step 5: Nitro Exploitation
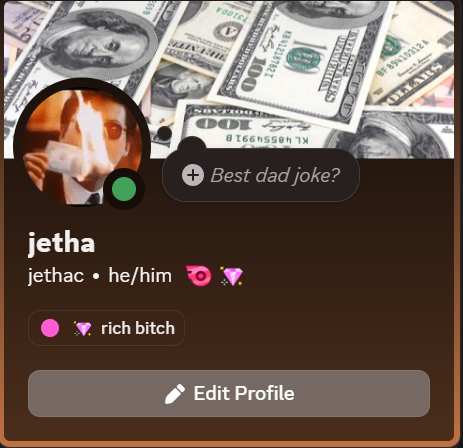
If the victim had Discord Nitro, their compromised account is pulled into a secondary Discord server ("confianza es 909") where they're tagged with humiliating roles:
- "rich bitch" (pink #FF5DD6) — Victims with Nitro subscriptions or payment methods
The attackers then exploit the victim's Nitro benefits — server boosts, animated emojis, higher upload limits — before eventually selling or abandoning the account.
Malware Technical Details
The ~164MB executable is an NSIS installer that drops a Java-based stealer into %APPDATA%\erkan\. It bundles its own JRE to avoid dependencies and uses Zelix KlassMaster obfuscation ($500+ commercial tool) to evade detection.
A license key (license-20251031231401-cba2) found in the payload indicates this is purchased malware-as-a-service — the attackers are customers of a stealer kit, not the original developers.
Discord Client Injection & Reinfection
Beyond stealing data, the malware injects persistent code into the Discord client at %APPDATA%\discord\. This injection survives Discord restarts and re-exfiltrates data every time the victim opens Discord.
Case Study: Victim Reinfected 6 Times in 4 Hours
One victim was compromised 6 separate times on the same day because they didn't know their Discord client was infected:
| Time | Event |
|---|
| 18:26 | Initial infection |
| 20:27 | Reopened Discord → reinfection (+2 hours) |
| 21:29 | Reopened Discord → reinfection (+1 hour) |
| 21:43 | Reopened Discord → reinfection (+14 min) |
| 22:24 | Reopened Discord → reinfection (+41 min) |
| 22:43 | Reopened Discord → reinfection (+19 min) |
The victim likely noticed something was wrong and restarted Discord or their computer, but this doesn't remove the injection. Each restart just triggered another exfiltration.
To fully remove the infection:
- Completely uninstall Discord (not just close it)
- Delete the entire folder:
%APPDATA%\discord\
- Delete the malware folder:
%APPDATA%\erkan\
- Reinstall Discord fresh from discord.com
Simply changing your password or enabling 2FA won't help if the Discord client itself is compromised — the injected code will steal your new credentials and session tokens immediately.
Technical Indicators (IOCs)
File Hashes (SHA256)
installer.exe ef38f3c3a3ba1114ed2336f2ab7c6f0a59f0f345fcf19385997f0edecca7c243
ysnd.jar afff725e321c7ef7d159b1895e2d131ea4161bfd74e306f6b776cbda6ecdc99f
swazla.exe f61fd2cf06604458a65f254642b531e985c2ca174999951f0a7830a356fae39f
Filesystem Artifacts
%APPDATA%\erkan\ # Installation directory
%APPDATA%\erkan\jre\bin\swazla.exe # Malicious Java launcher
%APPDATA%\ysnd.jar # Stealer payload
Malware Filenames
EldrynWorld.exe
Crushfall.exe
Furfall.exe
ChurryFall.exe
Recommendations
For Individuals
- Never run executables from Discord DMs, even from "friends" (accounts get compromised and used to spread malware)
- Don't save passwords in browsers — this is the primary target for stealers
- Password managers won't save you here — browser extensions get compromised along with the browser, and desktop-only password managers are also vulnerable since the malware has full system access. The only defense is not running the malware in the first place.
- Enable 2FA everywhere — preferably hardware keys or TOTP apps
- Be suspicious of "beta test" invitations for games with direct downloads
- Create your own Google Family group as a preemptive defense (you can't be added to another family)
- Create a Discord support account now at support.discord.com — attackers create support accounts with victim emails to block recovery. If you already have an account registered, they can't create one with your email.
For Game Developers
Attackers impersonate indie game developers to distribute malware. Protect your reputation and help players identify legitimate builds:
- Use distribution platforms with malware scanning:
- Steam — Steamworks provides secure distribution with built-in scanning, even for beta builds via Steam Playtest
- Epic Games Store — For larger releases, includes security vetting
- Google Play / TestFlight — Mobile platforms with mandatory security review
- Never share raw .exe files via Discord DMs, Google Drive, or direct downloads from personal websites
- Code sign your executables — Windows SmartScreen warnings make unsigned executables look suspicious (and rightfully so)
- Use closed beta platforms — Steam Playtest provides secure, trackable distribution for PC games
- Verify testers through established communities — Don't cold-DM strangers asking them to run executables; legitimate beta recruitment happens through Steam forums, Discord servers with history, or established gaming communities
Warning about itch.io: As of January 2026, itch.io does not scan uploaded executables for malware. The "ChurryFall" stealer in this campaign is actively being distributed through itch.io. Until itch.io implements malware scanning, treat all executable downloads from itch.io with the same caution as random Discord links. We urge itch.io to implement basic malware scanning to protect their community.
If someone claims to be a game developer and asks you to download an .exe directly, ask them to publish it on Steam instead. Legitimate developers will understand.
For Platform Security Teams
- Discord: Detect support account creation immediately after account compromise; flag token-based 2FA changes; treat CSAM reports with suspicion when they occur shortly after 2FA/password changes (may indicate weaponized false reports using compromised accounts)
- Google: Add friction to Family group additions when birthday was recently modified
- Vercel:
eldrynworld.com distributed malware — takedown required
- itch.io: "ChurryFall" malware is actively being distributed through the platform — implement malware scanning for all uploaded executables
Report To
| Entity |
Contact |
Report |
| Vercel |
vercel.com/abuse |
eldrynworld.com hosting |
| GoDaddy |
[email protected] |
Domain registration |
| itch.io |
itch.io/support |
ChurryFall malware distribution |
| Discord Trust & Safety |
In-app reporting |
Attacker accounts/servers |
| WhatsApp/Meta |
In-app reporting |
Turkish numbers used for ransom |