Update (January 6, 2026): The legitimate owner of the "jetha" account successfully recovered their account. Jetha was also a victim - their compromised account was used by the attackers to social engineer the victim and other targets.
Executive Summary
The victim (Discord: Nyakuza) was targeted through a compromised Discord account belonging to "jetha". The attacker used social engineering to deliver malware via a fake game link, then attempted to extort $500 from the victim. When they refused to pay, the attacker:
- Used the victim's compromised Discord account to spam child sexual abuse material (CSAM) solicitation messages in a group chat
- Screenshot the evidence they created
- Reported the victim's account to Discord for CSAM
- The victim's account was subsequently banned by Discord
WEAPONIZED FALSE REPORT: The attacker manufactured evidence of a ToS violation using the victim's own compromised account, then reported it to Discord.
Timeline of Events
Phase 1: Social Engineering (Dec 29, 7:13-7:23 PM JST)
The attacker, controlling the compromised "jetha" account, initiated contact with Nyakuza using a friendly, conversational approach:
7:17 PM
jetha:
how are you
7:18 PM
Nyakuza:
I'm going good. You?
7:18 PM
jetha:
doing alright yeah, bit tired but can't complain. been bouncing between game stuff and random projects as usual. what you been up to lately?
7:19 PM
Nyakuza:
Na not much just waiting for the turbo to go into the car and gaming
7:20 PM
jetha:
nice, that sounds like a good combo honestly. the wait for parts is always the worst part though. what have you been playing while you kill time?
7:21 PM
Nyakuza:
the parts a here it's just the shop is full at the moment so no room for my car. Been playing to much BF6 and Wuthering Waves atm
7:22 PM
jetha:
can i ask u a quick favor if you dont mind?
7:22 PM
Nyakuza:
yeah man go for it
7:22 PM
jetha:
I've been working on a small project with few friends for four weeks, 2d adventure one. can you take a look and give your review
7:23 PM
Nyakuza:
yeah bro
7:23 PM
jetha:
thanks man. https://www.eldrynworld.com/
7:23 PM
Nyakuza:
I'll try and break it
7:23 PM
jetha:
im waiting in lobby 2 in the game. all good
Analysis: The attacker built rapport by discussing gaming (BF6, Wuthering Waves) and cars before introducing the malicious link. The "EldrynWorld" site is one of several fake game sites used by the Micro Stealer operation to distribute malware.
Phase 2: Malware Execution & Extortion (Dec 29, 7:28-7:38 PM JST)
After Nyakuza downloaded and executed the malware, the attacker revealed their true intent:
7:28 PM
Nyakuza:
Who was you making this with?
7:29 PM
jetha:
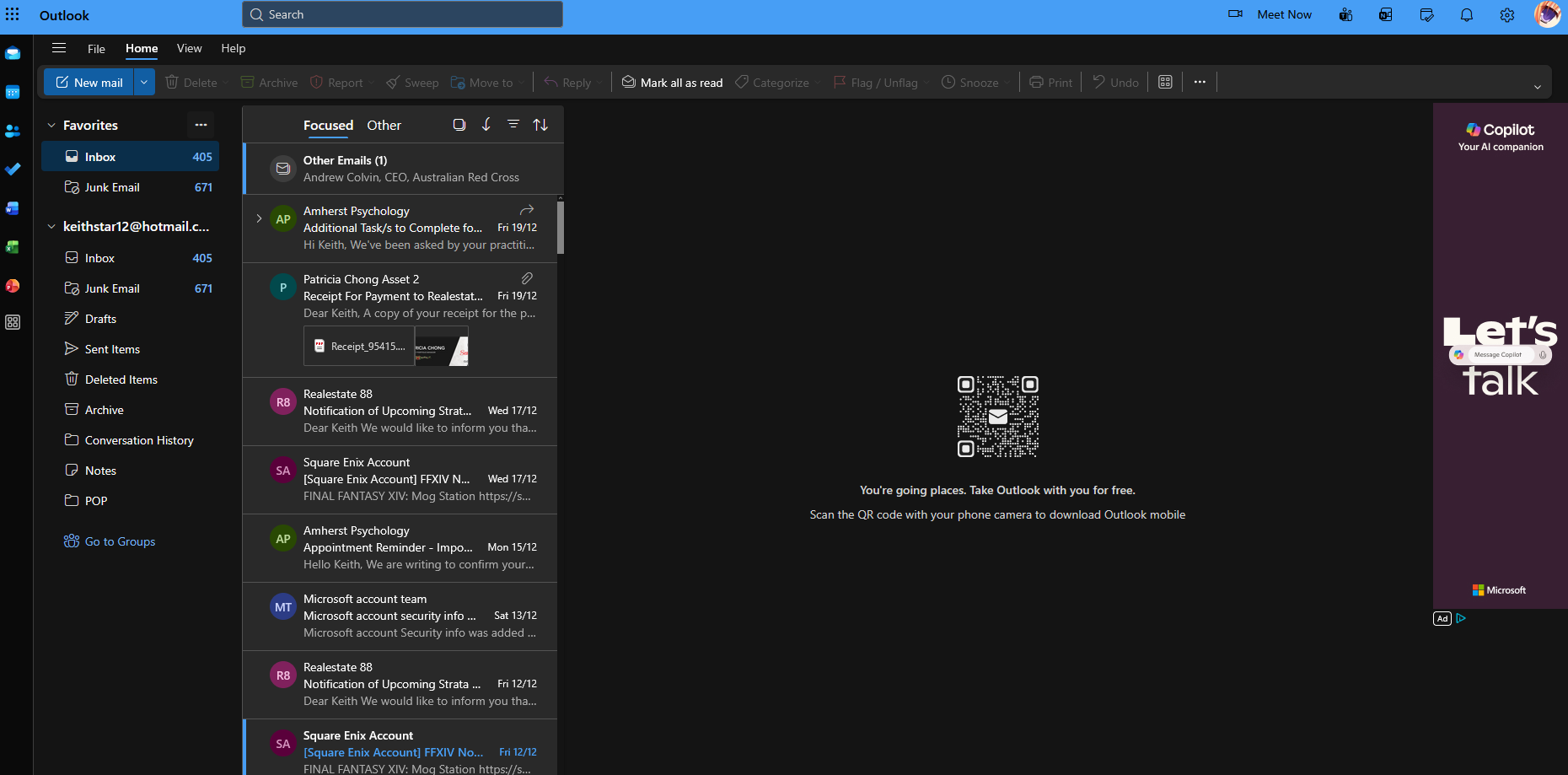
[Sends screenshot of victim's compromised email inbox]
Evidence #1
Screenshot showing attacker's access to victim's Hotmail inbox containing medical records, financial emails, and personal correspondence.
7:29 PM
jetha:
I've infected your computer's motherboard with a virus and you can't delete the virus until you buy new one. I have all your passwords, photos and accounts. If you dont pay, you can't use your computer anymore and i'll burn your motherboard and expose your Information on telegram. If you pay 500$, I'll delete your information on my database and the virus. Lastly I'll give you your accounts back and in the end, you won't see me anymore
7:29 PM
jetha:
yes or no. bro. If you say no, you'll lose your Discord too
7:31 PM
jetha:
think about it and give me your answer in 30 seconds. otherwise I will start the procedures
7:31 PM
jetha:
[Sends screenshot of manufactured CSAM evidence]
CRITICAL EVIDENCE #2
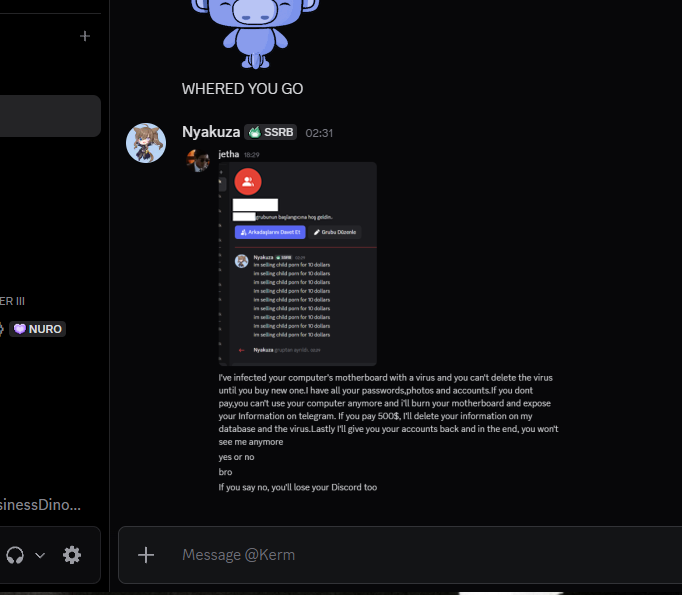
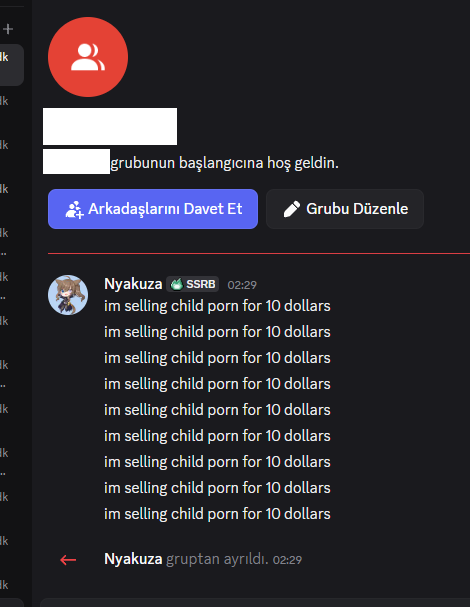
MANUFACTURED EVIDENCE: This screenshot shows the attacker using Nyakuza's compromised Discord account to spam "im selling child porn for 10 dollars" 9 times in a chat. The attacker created this "evidence" to use as leverage and later as the basis for a false report to Discord.
7:32 PM
jetha:
so are you paying. My aim is not to cause harm; I want the money
7:33 PM
Nyakuza:
I dont have the money. so no
7:33 PM
jetha:
Say goodbye to 11 years of memories
7:33 PM
jetha:
Work hard and buy yourself a new computer
7:34 PM
jetha:
I am reporting the messages. Finally, I am asking. Are you sure you won't pay?
7:37 PM
jetha:
BRO ANSWER ME ARE YOU PAYİNG YES OR NO
7:37 PM
Nyakuza:
I have nothing
7:37 PM
jetha:
HOW MUCH CAN YOU PAY
7:37 PM
Nyakuza:
I can do like $50
7:38 PM
jetha:
Do 200 and I'll let you go. fine?
7:38 PM
jetha:
borrow from someone. you'll lose a lot
7:38 PM
Nyakuza:
I'm not paying
Phase 3: Continued Harassment (Dec 30, 3:29-3:44 AM JST)
Hours later, the attacker returned:
3:29 AM
jetha:
[Sends second screenshot of email inbox]
Evidence #3
Second screenshot demonstrating continued access to the victim's Hotmail account, showing medical, financial, and personal emails.
3:29 AM
jetha:
im still here. dont worry
3:35 AM
jetha:
are you paying?
3:43 AM
jetha:
rip account. Your account will close in 10 minutes. I'll reopen it when you pay me
3:44 AM
Nyakuza:
I'm not paying
3:44 AM
jetha:
[Sends final image]
Evidence #4
Final image sent by attacker before executing the false report to Discord.
Evidence Analysis
Image 1: Compromised Email Access (7:29 PM)
The attacker demonstrated full access to the victim's Microsoft/Hotmail account by showing:
- Medical records: Emails regarding psychological assessments
- Financial data: Emails regarding property payments and strata notifications
- Gaming accounts: Square Enix/FFXIV account notifications
- Security alerts: Microsoft account security emails
- Personal contacts: Various personal correspondence
Image 2: Manufactured CSAM Evidence (7:31 PM)
CRITICAL EVIDENCE: This screenshot shows the attacker using Nyakuza's compromised Discord account to spam a group chat with the message:
"im selling child porn for 10 dollars"
The message was posted 9 times in rapid succession, followed by "Nyakuza gruptan ayrıldı" (Turkish: "Nyakuza left the group") - all at 02:29.
This is fabricated evidence. The attacker:
- Logged into Nyakuza's Discord using the stolen token
- Joined or used an existing group chat
- Spammed CSAM solicitation messages
- Left the group
- Screenshot the "evidence"
- Sent it to Nyakuza as leverage
- Later reported Nyakuza to Discord using this manufactured evidence
The False Report Mechanism
How It Worked
- Account Compromise: Attacker stole Nyakuza's Discord token via Micro Stealer malware
- Evidence Manufacturing: Using the stolen token, attacker logged into Nyakuza's account and posted CSAM solicitation messages
- Documentation: Attacker screenshot the messages they posted as "evidence"
- Extortion Leverage: Showed the screenshot to Nyakuza as proof of what they could do
- False Report: When Nyakuza refused to pay, attacker reported Nyakuza's account to Discord Trust & Safety using the manufactured evidence
- Account Ban: Discord, seeing apparent CSAM solicitation from the account, banned Nyakuza
Why This Is Particularly Malicious
- Victim is framed for a serious crime (CSAM distribution)
- Evidence appears legitimate - the messages did come from the account
- Discord's automated systems likely flagged and actioned the report quickly
- Victim has limited recourse - appealing a CSAM ban is extremely difficult
- Psychological harm - victim is now associated with child exploitation material
Victim Impact
The Victim (Nyakuza) Lost:
| Category |
Details |
| Discord Account |
11 years of history, memories, and connections |
| Community Standing |
Branded with a CSAM ban |
| Servers Owned |
Catshroom Army (40 members), Nyakuza Chan (16 members) |
| Servers Admin |
SHIREEEEEEEEEEEEEEEEEEEEEEEEEEEEE (5), Shimapan Hat (4), The League of J.O.N (18), the last braincell (7), great assets (28) |
| Privacy |
Medical, financial, and personal information exposed |
| Email Account |
Hotmail account compromised |
Data Stolen (from Micro Stealer logs):
- 1 password
- 887 cookies
- 3 autofill entries
- Discord token (used for the attack)
- 2 payment cards on Discord account
Attribution
The "jetha" account (Discord ID: 117097036242878465) was compromised and used by the Micro Stealer operation, a Turkish cybercrime group.
| Handle |
Role |
Real Name |
| 22v08 / 08v22 |
Ringleader |
GORKEM |
| p5ra / lea |
Active Operator |
Unknown |
| micro06888 |
Stealer Developer |
Unknown (student) |
Linguistic Evidence
- Turkish language in interface screenshots ("Nyakuza gruptan ayrıldı")
- Use of "PAYİNG" with Turkish dotted capital I (İ)
- Phrase construction consistent with non-native English speaker
Recommendations for the Victim
1. Document Everything
Save all evidence of the extortion and false report for potential legal action.
2. Appeal to Discord
File an appeal explaining the account was compromised and the CSAM messages were posted by the attacker. Use the template below.
4. Secure All Accounts
Change passwords on all accounts, especially email. Enable 2FA everywhere.
Legal Implications
The attacker committed multiple crimes:
- Computer Fraud: Unauthorized access to computer systems (Micro Stealer)
- Identity Theft: Using victim's accounts without authorization
- Extortion: Demanding payment under threat of harm
- False Report: Filing fraudulent abuse reports
- Defamation: Falsely associating victim with CSAM
- Cyberstalking: Continued harassment over hours
In Australia, this may violate:
- Criminal Code Act 1995 (Cth) - computer offenses
- Cybercrime Act 2001
- State stalking/harassment laws
Conclusion
The victim (Nyakuza) is completely innocent of the CSAM charges. The messages were posted by the attacker using the victim's stolen credentials, specifically to frame them and destroy their account when they refused to pay the ransom.
This case demonstrates a sophisticated weaponization of platform trust and safety mechanisms. The attacker:
- Compromised the victim via malware
- Manufactured evidence of serious ToS violations using the victim's own account
- Used the evidence for extortion
- Executed a false report when extortion failed




